

Injective Protocol is a decentralized exchange (DEX) platform that is built on the Ethereum blockchain. It aims to give users a smooth trading experience by letting them trade quickly, safely, and without trusting anyone else.
One thing that makes the Injective Protocol stand out is that users can trade any crypto or non-crypto asset without any limits. This is possible because the platform uses a new architecture called a "sidechain" to grow and support the trading of any asset.
User governance is another important part of the Injective Protocol. Its users run the platform and can vote on important decisions that affect how it grows and works. This ensures that the platform is open, based on the needs of its users, and driven by the community.

Injective Protocol also has a trading engine that is very fast and can handle thousands of trades per second. This is possible because the platform uses a layer-2 solution that lets it process transactions outside of the blockchain and settle them on the blockchain.
In terms of security, the Injective Protocol is made so that it can't be broken into or attacked. It protects user funds and keeps the platform's integrity using security measures like multi-signature wallets, auditing, and strict governance controls.
The Injective Protocol fixes several problems with traditional centralized exchanges (CEXs) and some decentralized exchanges already in place (DEXs).
Here are a few of the most important issues that the Injective Protocol tries to solve:
1. Centralization: Exchanges all in one place are more likely to be hacked, used for fraud, or attacked in other ways. Injective Protocol is a decentralized exchange, meaning a single organization does not run it. This makes it harder to hack or attack.
2. Support for a small number of crypto assets: Many decentralized exchanges in use today only support a small number of crypto assets. On the other hand, the Injective Protocol lets you trade any asset, whether it's a cryptocurrency or something else.
3. Slow transaction speeds: Because of the limitations of the Ethereum blockchain, some DEXs have slow transaction speeds and high fees. The Injective Protocol makes transactions fast and cheap using a new sidechain architecture and layer-2 solutions.
4. People often say that traditional centralized exchanges need to be more open and give users more power. Injective Protocol solves this problem by letting users run the platform and vote on important decisions about how it will grow and work.
5. Some DEXs only let you make simple spot trades, while others may only give you a few options for more advanced trading strategies. Injective Protocol offers many different ways to trade, such as futures, swaps that last forever, and more.
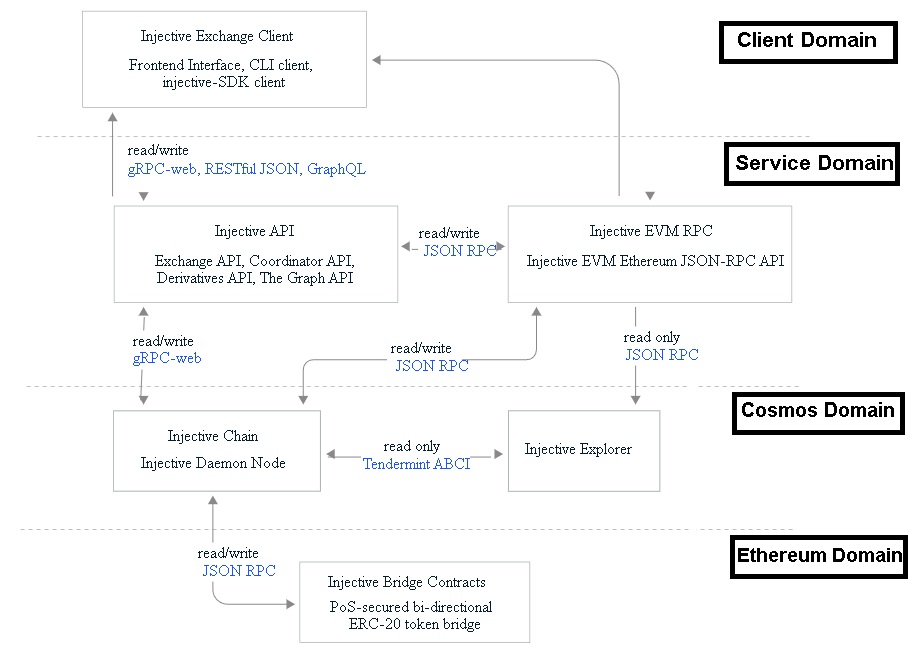
Injective Chain is a decentralized layer-2 scaling solution built on top of the Cosmos SDK that lets you trade any asset quickly, safely, and without any central control. It is the system that makes the decentralized exchange for Injective Protocol work.
Using a combination of layer-2 solutions, such as a sidechain architecture and a consensus mechanism based on Tendermint, Injective Chain is made to make trading fast and cheap. This lets the platform handle thousands of transactions per second while keeping security and decentralization high.
One of the most important things about an Injective Chain is that it can run any code. This means smart contracts written in any programming language can be run on it. This lets developers build complex financial apps and trading strategies on top of the platform.
The EVM (Ethereum Virtual Machine) execution environment is a runtime environment that runs smart contracts on the Ethereum blockchain. A sandboxed environment gives smart contracts written in the Solidity programming language a safe, separate place to run.
The EVM is a software-based virtual machine that runs on all Ethereum nodes, including miners, full nodes, and light clients. It is in charge of running the bytecode that is made from the Solidity code for a smart contract.
The EVM is made to be deterministic, which means that no matter what you put into it, it will always give you the same result. This is important to ensure smart contracts work as expected and can be checked for security flaws.
The EVM runs smart contracts by figuring out what the bytecode is that the Solidity code makes. It has instructions for running the bytecode, such as arithmetic operations, memory operations, and control flow instructions.
The Injective Exchange Client is software that lets people use the Injective Protocol decentralized exchange and trade on it. It has an easy-to-use interface with various trading tools and features that allow users to trade any asset quickly, safely, and fully decentralized.
The Injective Exchange Client is made to be easy to use. It has a simple and easy-to-understand interface that lets users move around the platform quickly and easily. It gives users a wide range of trading options, such as spot trading, futures trading, and perpetual swaps, as well as advanced trading tools like charting, order book analysis, and risk management.
The Injective Exchange Client also has a built-in wallet that lets users store their crypto assets safely and manage their funds on the platform. The wallet works with several popular cryptocurrencies and tokens and any asset that works on the decentralized Injective Protocol exchange.
One of the best things about the Injective Exchange Client is that it lets you trade between chains. With the cross-chain bridge technology of the Injective Protocol, users can trade any asset, no matter which blockchain it is on. This lets users trade assets not usually available on other decentralized exchanges.
The Injective API Provider is a software service that lets developers build apps on top of the Injective Protocol decentralized exchange. It gives developers a set of application programming interfaces (APIs) that they can use to connect to and interact with the Injective Protocol's underlying infrastructure.
The Injective API Provider is made to be flexible and easy to use. It has several APIs that support different kinds of applications and use cases. For example, it provides APIs for trading, market data, order management, and more.
Developers can use the Injective API Provider to make a wide range of applications, such as trading bots, tools for analyzing the market, and trading interfaces that are unique to each user. The APIs are available in various programming languages, such as Python, Java, and JavaScript. This makes it easy for developers to add them to their existing development environments.
One of the best things about the Injective API Provider is that it lets you trade between chains. This means that developers can use the cross-chain bridge technology of the Injective Protocol to make apps that let users trade any asset, no matter which blockchain it is on. This gives developers many new options for making decentralized finance (DeFi) applications.
The Injective Ethereum Bridge is a technology that lets assets move between the Injective Chain and the Ethereum blockchain. It is a two-way bridge that makes moving assets between the two chains easy. This opens up new possibilities for cross-chain trading and decentralized finance (DeFi) applications.
The Injective Ethereum Bridge works by locking assets on one Chain and creating equivalent assets on the other. For example, if a user wants to move ETH from the Ethereum blockchain to the Injective Chain, they would lock their ETH in a smart contract on the Ethereum blockchain, which would then mint an equal amount of eETH on the Injective Chain.
The Injective Ethereum Bridge is built on a decentralized and trustless architecture. This means that users can transfer assets without a central authority or intermediary. This is made possible by a complicated system of smart contracts and validators ensuring the asset transfers are honest and safe.
One of the best things about the Injective Ethereum Bridge is that it lets you trade between chains. This means that the decentralized exchange of the Injective Protocol can be used to trade any asset, no matter which blockchain it is on. For example, a user could trade eETH on the Injective Chain for BTC on the Bitcoin blockchain without the need for middlemen or centralized exchanges.
The Injective Ethereum Bridge also works with ERC-20 tokens, stablecoins, and other cryptocurrencies, among other things. Because of this, it is a powerful tool for developers who want to build cross-chain apps that need to transfer assets without any problems.
The native token for the Injective Protocol is called INJ. It is an ERC-20 token on the Ethereum blockchain. The INJ token is a very important part of how the Injective Protocol works and how the decentralized exchange is run.
The INJ token is used for many things, such as:
1. Payment of trading fees: Users who trade on the decentralized Injective Protocol exchange can use INJ tokens to pay their trading fees. Users who pay fees with INJ can get lower trading fees and other perks.
2. Staking and governance: Holders of INJ tokens can help run the Injective Protocol by staking their tokens and voting on important protocol decisions. This gives people who own INJ tokens a say in how the decentralized exchange grows and changes in the future.
3. Incentivization: The Injective Protocol gives rewards in the form of INJ tokens to users who take part in the network. This includes payments to liquidity providers, validators, and other people who take part in the network.
The maximum number of INJ tokens that can be made 100 million, and about 36 million are currently in circulation. The way INJ tokens are given out is meant to be fair and equal. Tokens are given to the Injective Protocol team, investors, and community members.
The community of validators who run the Injective Core Node software is in charge of how the Injective Protocol is run. Here is a simplified summary of how the Injective Protocol is run:
1. Proposals: Any community member can send a proposal to the network to request changes to the Injective Protocol. Proposals can be about new versions of protocols, changes to parameters, or any other changes to the network.
2. Discussion and Feedback: Once a proposal is sent in, the validators who use the Injective Protocol forum discuss and debate it. Feedback is given, suggestions for improvements are made, and the person who proposed can change it in response.
3. Voting: After a proposal has been discussed and changed, the validators on the Injective Protocol network put it to a vote. Validators can either vote for the proposal or against it.
4. Execution: If most validators agree that a proposal is good, it is implemented on the Injective Protocol network. This could mean making changes to the network's parameters, updating the protocol software, or making any other changes suggested by the community.
5. Monitoring: Once a proposal has been put into action, the validators on the Injective Protocol network watch how the changes affect things and make sure they work as planned. If problems arise, the validators can suggest and vote on changes to the network.
Overall, the Injective Protocol governance process is meant to be democratic and driven by the community, with proposals and changes being handled by network validators. This ensures that the network stays decentralized and flexible enough to meet the needs of its users. It also encourages growth and innovation within the Injective Protocol ecosystem.
The Injective Protocol development services are a group of services that the Injective Protocol team and third-party developers offer to help build and connect decentralized applications (DApps) to the Injective Protocol network. Here are some of these services:
1. SDKs: The Injective Protocol team offers a variety of software development kits (SDKs) for different programming languages. These SDKs let developers build and deploy DApps on the Injective Protocol network. These SDKs come with libraries, tools, and documentation that make it easier for developers to start building on the Injective Protocol.
2. Auditing of Smart Contracts: To ensure that DApps built on the Injective Protocol is safe and secure, developers can have third-party auditing firms check their smart contracts. These companies look at the code and architecture of the smart contract to find holes and other ways attackers might be able to break in.
3. Consulting and Support: The Injective Protocol team and third-party developers can help developers build and deploy DApps on the Injective Protocol network by offering consulting and support services. This includes advice on architecture, best development practices, and help to fix problems.
4. Training and Education: The Injective Protocol team offers training and educational resources to help developers learn how to build on the Injective Protocol network. This includes online courses, tutorials, and other learning materials that give a complete introduction to developing the Injective Protocol.
5. Integration Services: Developers outside Injective Protocol can offer integration services to help DApps connect to the network. This means making custom APIs and interfaces that let DApps talk to the Injective Protocol and use its features and functions.
Overall, the Injective Protocol development services offer a variety of tools and support to developers who want to build on the network. This helps the Injective Protocol ecosystem grow and be used by more people.
Conclusion
The Injective Protocol is a decentralized exchange platform on the Ethereum blockchain. It is made to offer fast, secure trading with no gas fees, which makes it a good choice for traders and developers who want a faster, cheaper way to trade cryptocurrencies. The Injective Protocol also offers several development services, such as SDKs, smart contract auditing, consulting and support, training and education, and integration services, to help its ecosystem grow and be used by more people. Overall, the Injective Protocol is a new platform that will likely play a big part in the growth of the decentralized finance (DeFi) industry in the coming years.